Crypto Audit Insider: Building vs. third-party software: Setting up an auditable back office
Our four experts David Byrd (EY), Steven Baum (Marcum), Alexis Tandéo (PwC), and Nicholas Newman (Harris & Trotter LLP) detail the infrastructure needed to set up an auditable back office and give you the best practices for using service providers.
For businesses leveraging digital assets, building an auditable back office can be a challenge due to the absence of internal control best practices in crypto. Streamlining back-office operations effectively requires the integration of tools and technology. There are several tools available for businesses leveraging crypto assets to complete back-office operations, such as block explorers, sub-ledgers, and internally developed systems that each bring different advantages and drawbacks.
Our esteemed experts from industry leaders EY, Marcum, PwC, and Harris & Trotter LLP offer pragmatic advice on establishing an auditable back office. They delve into the respective advantages of developing an internal back-office system and leveraging a sub-ledger, equipping finance leaders with pragmatic advice for a seamless audit journey.
Large transaction volumes require robust infrastructure
Companies with crypto financial activity can view on-chain transactions on the blockchain’s ledger or block explorers like Etherscan. However, explorers do not constitute an enterprise-grade system of records since there are often issues with data completeness and accuracy when using them. Additionally, there are challenges with scalability when using these tools. Businesses therefore need their own system of records for financial reporting, especially when facing an audit.
Nicholas Newman from Harris & Trotter LLP advises organizations with larger transaction volumes to carefully consider which infrastructure setup suits their needs:
“When it comes to tax, many entities are using their own software. However, the kind of software you can use depends on your transaction volumes and your business model. With larger transaction volumes, you need a complete dataset within the software you’re using to be able to review and account for big data”.
Businesses with large transaction volumes therefore need a scalable system with internal controls built-in to the solution to establish data completeness and accuracy.
Developing an internal back-office system is resource-intensive
Businesses integrating digital assets can choose between building their own back-office system or adopting existing sub-ledger software. However, building their own infrastructure often requires large teams and capital, making it less feasible for smaller companies.
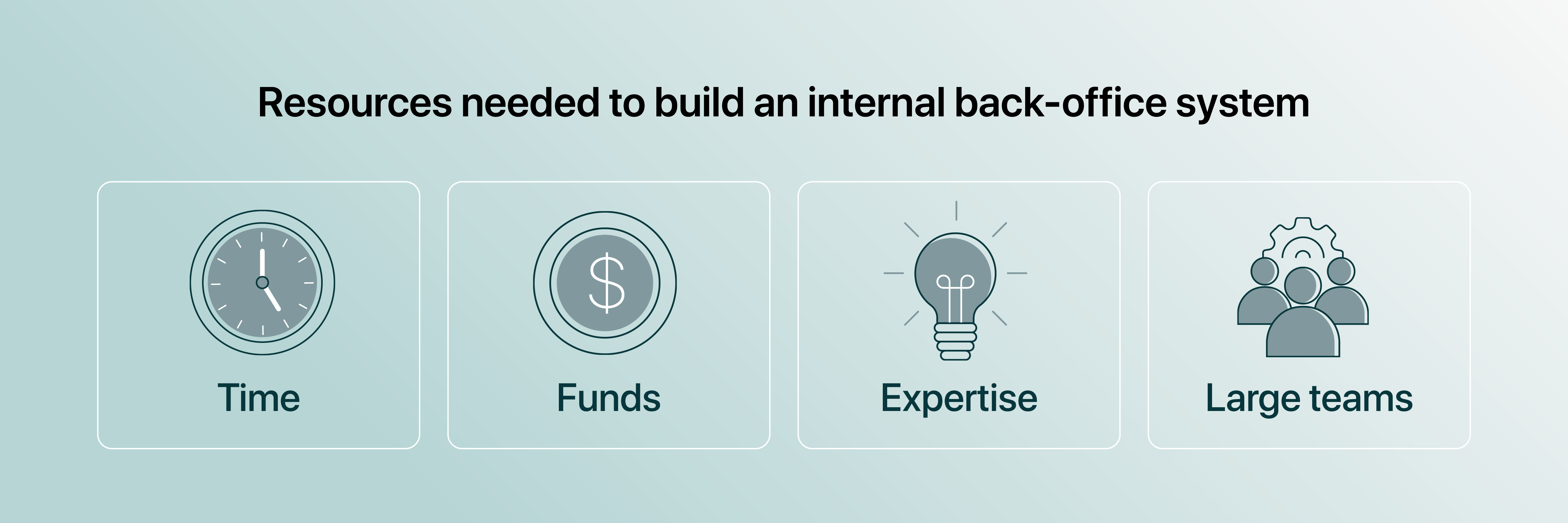
Steven Baum from Marcum explains the dilemma that many companies will face if they choose to build an internal back-office system:
“Many businesses operating in the crypto industry don’t have the necessary infrastructure in place to help them reach audit readiness. It takes time to build out these functions and the infrastructure. It’s not necessarily just about using capital to build this infrastructure, it’s a question of where you deploy it. And whether your business can deploy these resources away from other business functions to build this infrastructure.”
Maintaining an internally developed system is also resource-intensive, requiring teams to maintain API connectors to different sources (exchanges, blockchains, custodians) which change frequently. The teams that maintain internal infrastructure need to have the requisite skill and knowledge to handle technical issues around retrieving on-chain transactions. They therefore need deep crypto expertise to handle complex transactions like internal transfers that most commonly occur after smart contract execution.
In-house systems allow full control over financial data
While retrieving on-chain data can be challenging, internally developed infrastructure allows companies to have complete control over the system’s data. This means that businesses can organize the data in the most efficient way for their needs, rather than having to fit the template of an external provider.
Concerns around privacy may motivate businesses to rely on self-hosted infrastructure since all data is kept in-house with an internally developed system. However, given the difficulties around maintaining internal infrastructure, businesses might prefer to have a back-office system deployed locally into their system.
While internal systems offer independence from service provider downtime, they come with the burden of self-reliance. Keeping servers stable and updated 24/7 can be a daunting task for any back-office team, potentially leading to unwanted downtime on their terms. This reliance on self-maintained infrastructure can translate to greater vulnerability to outages and interruptions for businesses.
Sub-ledger software can help streamline back-office processes
In such cases, utilizing a sub-ledger solution such as Cryptio proves instrumental in automating various financial reporting processes, thereby reducing the workload associated with audit preparation for companies. Using a sub-ledger can also help reduce the work required by an auditor to test the reliability of financial statements provided by an audit client.
If the sub-ledger has an unqualified SOC 1 Type 2 report, auditors can more easily rely on the output of the system. This type of report provides reasonable assurance that the internal controls relevant to user entities’ financial reporting that the sub-ledger has in place are operational, meaning that auditors do not need to test the operating effectiveness of the controls. Since internally developed systems are not generally subjected to SOC audits, auditors would need to separately test the controls of those internally developed systems if taking a controls reliance approach.
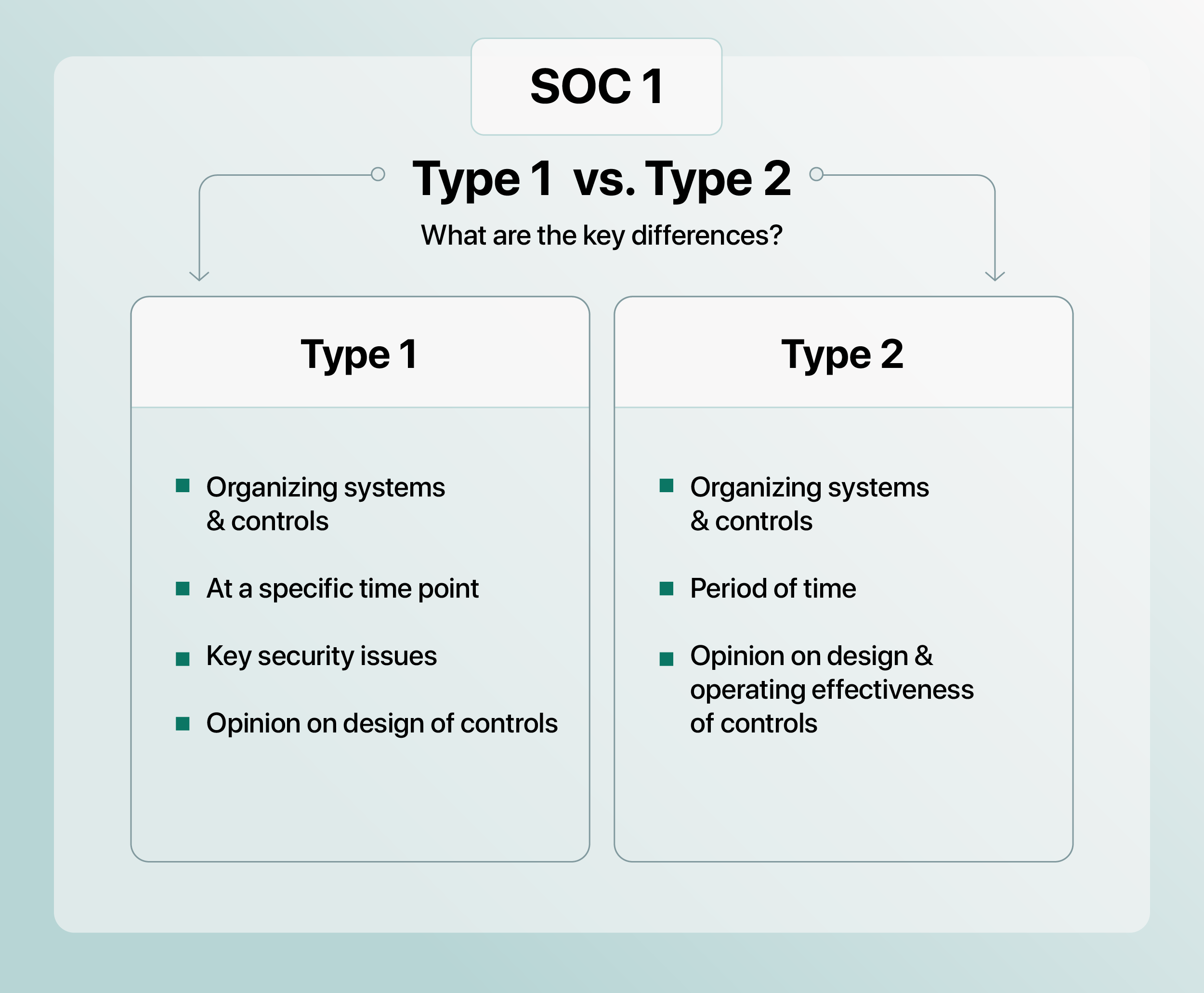
When there is an unqualified SOC 1 Type 2 report available, auditors can significantly reduce their level of substantive testing, reducing time spent on testing as well as audit fees. SOC 1 Type 1 reports are not, however, sufficient for auditors to reduce their time. These reports do not capture the operating effectiveness of the controls in place over a period of time, and thus force the auditor to either test client controls themselves, or to exclusively rely on substantive testing, each of which takes longer and causes audit fees to soar.
Back-office systems developed internally pose access, change and continuity risks
When a system is developed in-house, the organization assumes the responsibility of maintenance and future upgrades. This can pose higher risks around access, change, and continuity especially if development and knowledge are shared among a limited number of experts within the company
Alexis Tandéo of PwC highlights the substantial risks associated with auditable documentation when internally developing software:
"Building an in-house tool makes the company bear all the risks associated. The risk of access, change, and continuity can be significant. A comprehensive approach to monitoring movements and promptly adjusting access levels is essential to maintaining a secure and well-controlled environment. You must also proactively document for contingencies, particularly in the event of key resources involved in the system's development changing."
Internal controls to support an auditable back office
To mitigate the risks associated with internally developed systems, businesses need effective ITGC. These controls should cover the risks of:
- Access: ensure that only authorized users can access the system.
- Change: have policies in place that detail the process for when authorized users need to be added, modified, or removed from the system.
- Data security: verify that data is securely stored to prevent data breaches.
However, if finance teams are using third-party solutions to perform back-office operations, they must perform due diligence to ensure that the service provider has the appropriate controls in place by carefully analyzing the content of their SOC reports, especially the SOC 1 Type 2 report.
Service Organization Control (SOC) reports
A SOC report evaluates a service organization's controls related to security, availability, integrity, confidentiality, and privacy. SOC 1 report focuses on internal controls that may be relevant to a customer's financial reporting and is essential for sub-ledger software. Independent auditors issue these reports according to precise standards.
Alexis Tandéo of PwC explains that once a service provider is integrated, it is considered part of the organization by auditors.
“If an audit client is using a third-party service provider to support key financial information and reporting, our first question as an auditor will be to request if a SOC 1 Type 2 report is available for the solution and has been issued by a reliable and experienced independent auditor."
Once the reputation check is complete, auditors examine the scope of the report and ensure that testing carried out for the report covers the entire audited period.
Complementary user entity controls (CUECs)
These controls are implemented at the user level to ensure that businesses using a third-party solution can have better control over how the service provider and its services are used. Additionally, they make sure that the user’s access remains within the scope agreed upon by both organizations.
The CUECs required to support an auditable back office differ between business models however David Byrd from EY outlines key considerations to help businesses determine the CUECs needed:
- Authorization policies and procedures to assure that transactions are authorized, secure, complete, and timely.
- Data transmission policies and procedures to protect data by appropriate methods, like encryption.
- Separation procedures occur in the form of regular account assessments and timely account removal.
- Physical access controls notify the service provider when access is to be added, modified, or revoked for an employee of the user entity.
- Security procedures refer to monitoring or updating antivirus infrastructure, applying security patches, and related controls.
Audit-ready from the start: Setting up an auditable back office
Businesses with on-chain activity face numerous challenges in building an auditable back office. While finance teams may develop their own system, this approach comes with various obstacles such as the intense resource constraints to build it. If companies leveraging digital assets use an internally developed system, they should implement ITGC controls to mitigate risks such as data breaches, fraud, and manipulation of financial records.
Sub-ledger software therefore can help businesses with on-chain activity to automate back-office processes and to implement internal controls. Businesses considering a sub-ledger should analyze their SOC 1 (Type 1 and 2) reports before deciding upon it, ensuring that the service provider has the appropriate controls in place and is following best practices around back-office operations. Upon implementation of a third-party solution, businesses must also ensure that their CUECs are effective in keeping their use of the service provider within the scope of their mutual agreement.
Discover the Crypto Audit Insider series:
- Introduction to our experts.
- How to structure your team for audit success.
- Internal controls for data completeness and accuracy.
- Internal controls for treasury operations, custody, and payments.
About David Byrd, Partner, EY
David is a Partner at EY and the firm’s Blockchain Strategy Leader for Assurance. His role involves guiding asset managers, banks, exchanges, and custodians in achieving their goals within the blockchain and digital asset landscape. Leading EY's Digital Asset Research Center, he oversees teams dedicated to supporting Assurance, Tax, and Consulting initiatives. With an in-depth technical grasp of blockchain technology and custody solutions, David actively contributes to the development of digital asset tools used by EY for audit and audit readiness engagements. Additionally, he communicates with regulators worldwide and prominent industry associations to exchange insights and foster best practices in the realms of accounting, auditing, compliance, and digital asset valuation.
About Steven Baum, Partner, Marcum
Steven is a Certified Public Accountant, Partner at Marcum LLP and serves as the Digital Asset and Blockchain Industry Co-Leader. Steven has close to 15 years of experience working with a wide range of industries, most notably digital assets and technology. Steve is known for his expertise in assisting businesses with transactional engagements, including IPO's, Token Launches, reverse mergers, Private Placement Offerings, and mergers/acquisitions, but also for his charismatic business acumen. You can find Steve at many industry conferences, speaking and connecting with industry leaders. Steve holds a BS in Accounting from Hofstra University and a Master's in Accountancy from Rutgers University.
About Alexis Tandéo, Director - Digital Assets Trust Services, PwC
Alexis Tandéo is a Director at PwC in its Digital Assets Trust Services practice. He provides various services to institutional clients, corporations and startups to help them navigate the challenges of digital asset management. He supports some of the industry’s largest players to implement internal controls that address the risks inherent in crypto businesses. Additionally, he consults on financial reporting compliance requirements for companies in the crypto realm and provides accounting and regulatory reviews.
About Nicholas Newman, Partner, Harris & Trotter LLP
Nicholas Newman is a Partner & Head of Digital Assets at Harris & Trotter LLP, leading the firm’s digital assets practice. He works with some of the most prominent entities in the crypto industry including 1inch, Wintermute, and Blockchain.com, supporting them with audit, advisory, accounting, bookkeeping, compliance, and taxation services. With expertise in crypto and audit, he is able to support companies with diverse cases, shape regulatory frameworks and collaborate globally as an independent member of BKR and community-led interest groups like Web3CFO. Nicholas championed Harris & Trotter LLP's innovative Proof of Reserve service powered by Chainlink, ensuring transparency in clients' on-chain and off-chain reserves, bolstering their financial credibility.
Table of contents
- Large transaction volumes require robust infrastructure
- Developing an internal back-office system is resource-intensive
- In-house systems allow full control over financial data
- Sub-ledger software can help streamline back-office processes
- Back-office systems developed internally pose access, change and continuity risks
- Internal controls to support an auditable back office
- Audit-ready from the start: Setting up an auditable back office